To control access to a system we need firewalls. A firewall is a device (usually a router or a computer) installed between the internal network of an organization and the rest of the Internet. It is designed to forward some packets and filter (not forward) others. Figure shows a firewall.
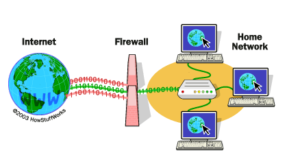
For example, a firewall may filter all incoming packets destined for a specific host or a specific server such as HTTP. A firewall can be used to deny access to a specific host or a specific service in the organization. A firewall is usually classified as a packet-filter firewall or a proxy-based firewall.
Packet-Filter Firewall
A firewall can be used as a packet filter. It can forward or block packets based on the information in the network-layer and transport-layer headers: source and destination IP addresses, source and destination port addresses, and type of protocol (TCP or UDP). A packet-filter firewall is a router that uses a filtering table to decide which packets must be discarded (not forwarded). Figure 32.33 shows an example of a filtering table for this kind of a firewall.
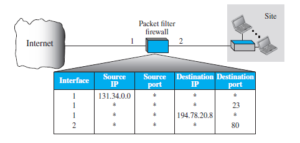
According to the figure, the following packets are filtered:
- Incoming packets from network 131.34.0.0 are blocked (security precaution). Note
that the * (asterisk) means “any.” - Incoming packets destined for any internal TELNET server (port 23) are blocked.
- Incoming packets destined for internal host 194.78.20.8 are blocked. The organization
wants this host for internal use only. - Outgoing packets destined for an HTTP server (port 80) are blocked. The organization
does not want employees to browse the Internet.
A packet-filter firewall filters at the network or transport layer.
Proxy Firewall
The packet-filter firewall is based on the information available in the network layer and transport layer headers (IP and TCP/UDP). However, sometimes we need to filter a message based on the information available in the message itself (at the application layer). As an example, assume that an organization wants to implement the following policies regarding its web pages: only those Internet users who have previously established business relations with the company can have access; access to other users must be blocked. In this case, a packet-filter firewall is not feasible because it cannot distinguish between different packets arriving at TCP port 80 (HTTP). Testing must be done at the application level (using URLs).
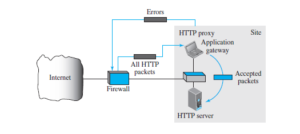
A proxy firewall filters at the application layer.





![[HINDI] What is DoS attack and DDoS attack?](https://bittentechsolutions.in/wp-content/uploads/2020/04/ddos-218x150.jpg)
![[HINDI] What is juice jacking? Think twice before using public USB ports](https://bittentechsolutions.in/wp-content/uploads/2020/04/juice-jacking-risk-1200x675-1-218x150.jpg)








nice
Nice article on firewall
Nice and perfect article of Firewall and DoS it’s really like that.
Nice post with a great quality of content. This is really helpful content. Thanks for sharing such a informative information..