Information security sometimes shortened to Infosec. It is not all about securing information from unauthorized access.Basically,Information Security is the practice of preventing unauthorized access modification and destruction of information. Information can be physical or electrical one. Information can be anything like your details or we can say your profile on social media, your data in mobile phone, your biometrics etc. Therefore, Information Security spans so many research areas like-
Cryptography, Mobile Computing, Cyber Forensics, Online Social Media etc.
During First World War, Multi-tier Classification System was developed keeping in mind
sensitivity of information. With the beginning of Second World War formal alignment of Classification System was done. Alan Turing was the one who successfully decrypted Enigma Machine which was used by Germans to encrypt warfare data. Information Security programs are builds around main 3 objectives, commonly known as CIA –
Confidentiality, Integrity, and Availability.
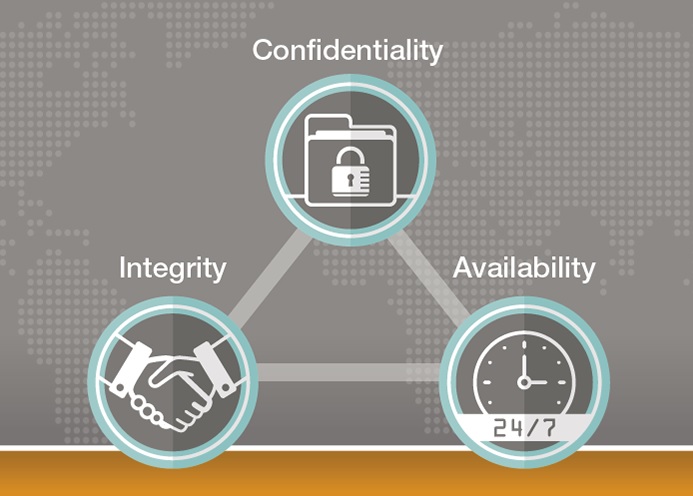
1. Confidentiality
It means information is not disclosed to unauthorized individuals, entities and process. For example if we say I have a password for my Gmail account but someone saw while I was doing a login into Gmail account. In that case my password has been compromised and Confidentiality has been breached.
2. Integrity
Integrity means maintaining accuracy and completeness of data. This means data cannot be edited in an unauthorized way. For example if an employee leaves an organization then in that case data for that employee in all departments like accounts, should be updated to reflect status to JOB LEFT so that data is complete and accurate and in addition to this only authorized person should be allowed to edit employee data.
3. Availability
Availability means information must be available when needed. For example if one needs to access information of a particular employee to check whether employee has outstand the number of leaves, in that case it requires collaboration from different organizational teams like network operations, development operations, incident response and policy/change management.
Denial of service attack is one of the factors that can hamper the availability of information.
Types of InfoSec
Cloud security
It is focuses on building and hosting secure applications in cloud environments and securely consuming third-party cloud applications. “Cloud” simply means that the application is running in a shared environment. Businesses must make sure that there is adequate isolation between different processes in shared environments.
Cryptography
Encrypting data in transit and data at rest helps ensure data confidentiality and integrity. Digital signatures is commonly used in cryptography to validate the authenticity of data. Cryptography and encryption has become increasingly important. A good example of cryptography use is the Advanced Encryption Standard (AES). The AES is a symmetric key algorithm used to protect classified government information.
Infrastructure security
Infrastructure security deals with the protection of internal and extranet networks, labs, data centers, servers, desktops, and mobile devices.
Incident response
Incident response is the function that monitors for and investigates potentially malicious behavior. In preparation for breaches, IT staff should have an incident response plan for containing the threat and restoring the network. In addition, the plan should create a system to preserve evidence for forensic analysis and potential prosecution. This data can help prevent further breaches and help staff discover the attacker.
Vulnerability management
Vulnerability management is the process of scanning an environment for weak points (such as unpatched software) and prioritizing remediation based on risk. In many networks, businesses are constantly adding applications, users, infrastructure, and so on. For this reason, it is important to constantly scan the network for potential vulnerabilities.
Finding a vulnerability in advance can save your businesses the catastrophic costs of a breach.


![[HINDI] What is DoS attack and DDoS attack?](https://bittentechsolutions.in/wp-content/uploads/2020/04/ddos-218x150.jpg)
![[HINDI] What is juice jacking? Think twice before using public USB ports](https://bittentechsolutions.in/wp-content/uploads/2020/04/juice-jacking-risk-1200x675-1-218x150.jpg)



![[HINDI] Invest in bitcoin and play with millions](https://bittentechsolutions.in/wp-content/uploads/2020/05/photo-1550565360-6986a92b7169-218x150.jpg)


![[HINDI] What is DoS attack and DDoS attack?](https://bittentechsolutions.in/wp-content/uploads/2020/04/ddos-100x70.jpg)
![[HINDI] USA fake WhatsApp number trick for complete anonymity](https://bittentechsolutions.in/wp-content/uploads/2020/04/1-100x70.png)


![[HINDI] What is juice jacking? Think twice before using public USB ports](https://bittentechsolutions.in/wp-content/uploads/2020/04/juice-jacking-risk-1200x675-1-100x70.jpg)