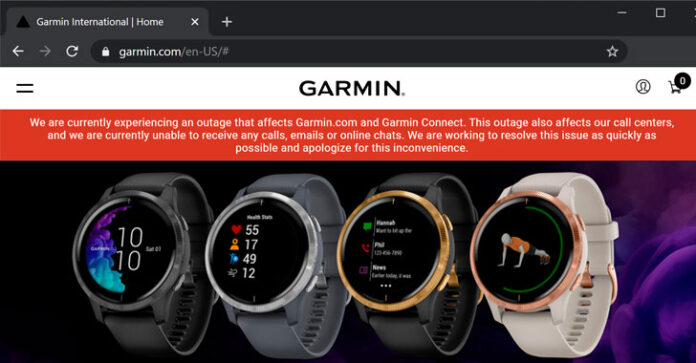
Garmin, the creator of wellness trackers, smartwatches and GPS-based wearable gadgets, is right now managing an enormous overall assistance interference subsequent to getting hit by a focused on ransomware assault, a representative of the organization disclosed to The Hacker News on state of secrecy.
The organization’s site and the Twitter account say, “We are at present encountering a blackout that influences Garmin.com and Garmin Connect.”
“This blackout likewise influences our call places, and we are right now unfit to get any calls, messages or online visits. We are attempting to determine this issue as fast as could be expected under the circumstances and apologize for this burden.”
Thus, the organization yesterday had to incidentally close down a portion of its associated administrations, including Garmin Express, Garmin Connect versatile, and the site—limiting a huge number of its clients from getting to the cloud benefits or in any event, adjusting their watches locally to the application.
In spite of the fact that very little data is accessible on details of the digital assault, some neighborhood media reports guarantee programmers have figured out how to bargain the organization’s application and database servers with ransomware.
It additionally says Garmin has sent declarations to its IT staff in Taiwan-based industrial facilities reporting the following two days of arranged support, i.e., July 24 and 25.
Different sources in the cybersecurity network recommend that the cyberattack may have included WastedLocker, one of the focused on ransomware posse, known as the Evil Corp or Dridex.
Garmin ransomware assault
The business as usual of the aggressors behind WastedLocker includes trading off corporate systems, performing benefit heightening, and afterward utilizing sidelong development to introduce ransomware on significant frameworks before requesting a great many dollars in emancipate installment.
As per specialists at SentinelOne, WastedLocker is a generally new ransomware family dynamic throughout the previous not many months and has since been assaulting high-esteem focuses over various enterprises.
WastedLocker utilizes JavaScript-based SocGholish toolset to convey payload by taking on the appearance of framework or programming refreshes, misuses UAC sidestep strategies to raise benefits, and use Cobalt Strike for horizontal developments.
“All the security innovation on the planet won’t ensure against decided aggressors. 97% of misfortunes originate from socially-designed assaults and over 90% are started by email,” Lucy Security CEO Colin Bastable imparted a remark to The Hacker News.
“There are no bleeding edges in cyberwarfare – we are for the most part reasonable game for agitators, and no element or individual is protected from digital assault. Train your kin to recognize and oppose ransomware assaults – similarly as you fix frameworks, fix your kin with normal, fluctuated, constant and all around arranged security mindfulness preparing to make them part of your resistances,” Bastable included.
Gurucul CEO Saryu Nayyar additionally recommended the equivalent:
“You simply don’t have the foggiest idea when the trouble makers are going to assault and who will be their next casualty. In any case, what we do know is each association is defenseless to ransomware assaults.”
“Along these lines, do what you can to get ready and react. Ideally, Garmin has an every day reinforcement routine for the organization’s frameworks and information. That is table stakes. On the off chance that you get hit, at any rate you can recoup your information.”
Garmin has not yet formally affirmed whether the occurrence is a ransomware assault or not, yet we have reached the organization and will refresh the story when we get more data on this episode.





![[HINDI] What is DoS attack and DDoS attack?](https://bittentechsolutions.in/wp-content/uploads/2020/04/ddos-218x150.jpg)
![[HINDI] What is juice jacking? Think twice before using public USB ports](https://bittentechsolutions.in/wp-content/uploads/2020/04/juice-jacking-risk-1200x675-1-218x150.jpg)