Introduction
Cybersecurity is the protection of Internet-connected systems, including hardware, software, and data from cyber-attacks. It can be made up of two words one is cyber, and the other is security. Cyber is meant to the technology which contains systems, network and programs or data. And security related to the protection, which includes systems security, network security and application, and information security.
Cybersecurity is the practice of protecting systems, networks, and programs from attacks. These cyber-attacks are usually aimed at accessing, changing, or destroying sensitive information extorting money from users or interrupting the normal business process.
Implementing effective cybersecurity measures is particularly challenging today because there are more devices than people, and attackers are becoming more innovative.
Types of Cyber-Attacks in This Era
Malware: Malware is any software designed or created to damage a computer, server, or network.
Phishing: Phishing is the attempt to capture sensitive information such as usernames, passwords, and credit/debit card details by electronic communication. Attackers used a clone or fake website, which looks the same as the original one.
Password attack: password attack is the process of recovering passwords from data that have been stored in the computer system. A typical attack in a password attack is brute-force, and it is used to repeatedly try guesses for the password and check them in a cryptographic hash of the password.
Denial of Service (DDoS) attack: Denial of service attack is a cyber-attack in which he/she illegally find to overwhelm them with more traffic than the server can hold. The main reason is the fake packets.
Man in The Middle Attack (MITM): Man in the middle attack is an attack which the attacker secretly communicate and possibly change the communications between two parties who believe that they are directly communicating with each other.
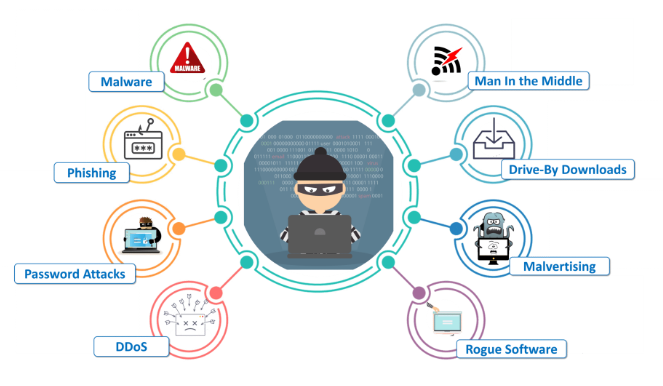
Drive-by download: Drive-by downloads may happen when visiting a website, opening an e-mail attachment or clicking a link, or clicking on a misleading pop-up window by clicking on the window in the mistaken belief that.
Malvertising: Malversiting is used by online advertising to spread malware.
Rogue Software: Rogue software is a form of malicious software and internet fraud that misleads users to believe that there is a virus on their computer and try to convince them to pay for a fake malware removal tool or a phony antivirus that has malware and installs on their computer.
Importance of Cyber Security
In today’s connected world, everyone benefits from advanced cyber defense programs. At an individual level, a cybersecurity attack can result in everything from identity theft, to extortion attempts, to the loss of essential data like family photos. Everyone relies on critical infrastructures like power plants, hospitals, and financial service companies. Securing these and other organizations is essential to keeping our society functioning.
Cyber-attack are now an international concern and have given many concerns that hacks and other security attacks could endanger the global economy. Organizations transmit sensitive data across networks and to other devices in the course of doing business, and Cybersecurity describes to protect that information and the systems used to process or store it.
As the volume of cyber-attacks grows, companies and organizations, especially those that deal with information related to national security, health, or financial records, need to take steps to protect their sensitive business and personal information.
How is Cybersecurity implemented?
There are three main steps to fix a security issue:
Step 1: Recognize the problem that is causing the security issue; for example, we have to recognize whether there is a denial of service attack or a man in the middle attack.
Step 2: Evaluate and analyze the problem. We have to make sure we isolate all the data and information that may have been compromised in the attack.
Step 3: Develop a patch that actually solves the problem and brings back the organization to a running state.
Elements of cybersecurity
Ensuring cybersecurity requires the coordination of security efforts made throughout an information system, including:
- Application security
- Information security
- Network security
- Disaster recovery/business continuity planning
- Operational security
- End-user education
It can be a challenge in cybersecurity to keep up with the changing of security risks. The traditional approach has been to focus resources on crucial system components and protect against the biggest known threats, which meant leaving elements undefended and not protecting systems against less dangerous risks.
To deal with the current environment, advisory organizations are promoting a more proactive and adaptive approach. The National Institute of Standards and Technology (NIST), for example, issued updated guidelines in its risk assessment framework that recommend a shift toward continuous monitoring and real-time assessments.
Framework for Improving Critical Infrastructure version 1.1 released in April 2018. The voluntary cybersecurity framework, developed for use in the banking, communications, defense, and energy industries, can be adopted by all sectors, including federal and state governments. President Donald Trump issued an executive order mandating that federal agencies took the NIST Cybersecurity Framework (NIST CSF) in May 2017.
As a result of security risks, investments in cybersecurity technologies and services are increasing. In the past, Gartner had predicted that worldwide spending on information security products and services would grow to $114 billion in 2018, and another 8.7% increase to $124 billion in 2019. Later, in 2019, Gartner had also predicted spending in enterprise security and risk management to grow 11% in 2020 regarding the Middle East and North Africa.
Benefits of cybersecurity
Benefits of utilizing cybersecurity includes:
- Business protection against malware, ransomware, phishing, and social engineering.
- Protection for data and networks.
- Prevention of unauthorized users.
- Improves recovery time after a breach.
- Protection for end-users.
- Improved confidence in the product for both developers and customers.
Cybersecurity challenges
Cybersecurity challenged by hackers, data loss, privacy, risk management, and changing cybersecurity strategies. Nothing currently indicates that cyber-attacks will decrease. Moreover, with the more entry points, there are for attacks, the more cybersecurity needs to secure networks and devices.
One of the most problematic elements of cybersecurity is the continually evolving nature of security risks. As new technologies emerge, and tech used in new or different ways, new avenues of attack developed as well. Keeping up with these continual changes and advances in attacks can be challenging to organizations, as well as updating their practices to protect against them. It also includes ensuring that all the elements of cybersecurity are continually changed and updated to protect against potential vulnerabilities. It can be especially challenging for smaller organizations.
Additionally, today, there is a lot of potential data that an organization can gather on individuals who take part in one of their services. With more data collected, the likelihood of a cybercriminal who wants to steal personally identifiable information is another concern. For example, an organization that stores personally identifiable information in the cloud may be subject to a ransomware attack, and should do what they can to prevent a cloud breach.
Cybersecurity should also address end-user education, as an employee may accidentally bring a virus into a workplace on their work computer, laptop, or smartphone.
Another massive challenge to cybersecurity includes a job shortage. As growth in data from businesses become more important, the need for more cybersecurity personnel to analyze, manage, and respond to incidents increases. It estimated that there are two million unfilled cybersecurity jobs worldwide. Cybersecurity Ventures also forecasts that by 2021, there will be up to 3.5 million unfilled cybersecurity jobs.
However, new advances in machine learning and artificial intelligence (AI) have started to developed to help in organizing and managing data — although not to the effect needed.
Automation
AI and machine learning in areas that have high-volume data streams and can help in areas such as:
- Correlating data- which focuses on organizing data, identifying possible threats within data, and predicting an attack’s next step.
- Detecting infections- which focuses on having a security platform analyze data, recognize threats as well as create and enact security protections.
- Generating protections- without putting a strain on resources.
- Implementing protections.
Cybersecurity vendors
Vendors in cybersecurity fields will typically use the endpoint, network, and advanced threat protection security as well as data loss prevention. Three commonly known cybersecurity vendors include Cisco, McAfee, and Trend Micro.
Cisco tends to focus on networks and allows its customers to utilize firewalls, VPNs, and advanced malware protection along with supporting email and endpoint security. Cisco also supports real-time malware blocking.
Trend Micro is an anti-malware vendor that offers threat protection for mobile, hybrid clouds, SaaS, and the IoT. Trend Micro provides users with endpoint, email, and web security.
Careers in cybersecurity
As the cyber threat landscape continues to grow and emerging threats — such as the threats on the view of the internet of things — individuals needed with the required skills and awareness in both hardware and software skills.
IT professionals and other computer specialists are needed in security jobs, such as:
- Chief information security officer (CISO): This individual implements the security program across the organization and oversees the IT security department’s operations.
- Security engineer: This individual protects company assets from threats with a focus on quality control within the IT infrastructure.
- Security architect: This individual is responsible for planning, analyzing, designing, testing, maintaining, and supporting an enterprise’s critical infrastructure.
- Security analyst: This individual has several responsibilities that include planning security measures and controls, protecting digital files, and conducting both internal and external security audits.
Common types of cybersecurity
Network Security protects network traffic by controlling incoming and outgoing connections to prevent threats from entering or spreading on the network.
Data Loss Prevention (DLP) protects data by focusing on the location, classification, and monitoring of information at rest, in use and motion.
Cloud Security protects data used in cloud-based services and applications.
Intrusion Detection Systems (IDS) or Intrusion Prevention Systems (IPS) work to identify potentially hostile cyber activity.
Identity and Access Management (IAM) use authentication services to limit and track employee access to protect internal systems from malicious entities.
Encryption is the process of encoding data to render it unintelligible and is often used during data transfer to prevent theft in transit.
Antivirus/anti-malware solutions scan computer systems for known threats. Modern solutions are even able to detect previously unknown threats based on their behavior.
Cybersecurity is constantly evolving
Traditional cybersecurity centers around the implementation of defensive measures around a defined perimeter. Recent enablement initiatives like remote workers and Bring Your Own Device (BYOD) policies have dissolved the boundary, reduced visibility into cyber activity, and expanded the attack surface. Today, breaches are increasing at a rapid pace despite record levels of security spending. Global organizations are turning to human-centric cybersecurity, a new approach that places focus on changes in user behavior instead of an exponential number of growing threats. Founded on behavior analytics, human-centric cybersecurity provides insight into how an end-user interacts with data and extends security controls into all the systems where data resides, even if not exclusively controlled by the organization. Ultimately, this approach design to identify behavioral anomalies to surface and prioritize the most severe threats, reducing investigation, and threat detection times.





![[HINDI] What is DoS attack and DDoS attack?](https://bittentechsolutions.in/wp-content/uploads/2020/04/ddos-218x150.jpg)
![[HINDI] What is juice jacking? Think twice before using public USB ports](https://bittentechsolutions.in/wp-content/uploads/2020/04/juice-jacking-risk-1200x675-1-218x150.jpg)








make video on ASCII encrption on your yotube channel sir.
Sure Sushant Ansh bhaiya will make a video. Thanks for your comment.