Cybersecurity specialists have found basic weaknesses in modern VPN usage basically used to give distant access to operational innovation (OT) systems that could permit programmers to overwrite information, execute noxious code, and bargain mechanical control frameworks (ICS).
Another report distributed by modern cybersecurity organization Claroty shows numerous extreme weaknesses in big business grade VPN establishments, including Secomea GateManager M2M Server, Moxa EDR-G902, and EDR-G903, and HMS Networks eWon’s eCatcher VPN customer.
These weak items are generally utilized in field-based ventures, for example, oil and gas, water utilities, and electric utilities to distantly get to, keep up and screen ICS and field gadgets, including programmable rationale controllers (PLCs) and information/yield gadgets.
As indicated by Claroty scientists, fruitful abuse of these weaknesses can give an unauthenticated assailant direct access to the ICS gadgets and possibly cause some physical harm.
In Secomean’s GateManager, analysts revealed various security defects, including a basic weakness (CVE-2020-14500) that permits overwriting discretionary information, executing self-assertive code, or causing a DoS condition, running orders as root, and getting client passwords because of the utilization of a powerless hash type.
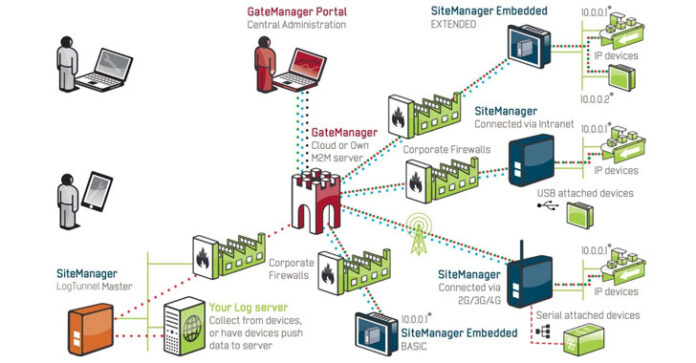
GateManager is a broadly utilized ICS far off access worker sent worldwide as a cloud-based SaaS arrangement that permits clients to interface with the inner system from the web through a scrambled passage while keeping away from worker arrangements.
hacking vpn worker
The basic blemish, distinguished as CVE-2020-14500, influences the GateManager segment, the fundamental directing example in the Secomea far off access arrangement. The defect happens because of ill-advised treatment of a portion of the HTTP demand headers gave by the customer.
This blemish can be misused distantly and without requiring any verification to accomplish far off code execution, which could bring about increasing full access to a client’s inside system, alongside the capacity to unscramble all traffic that goes through the VPN.
In Moxa EDR-G902 and EDR-G903 mechanical VPN workers, scientists found a stack-based support flood bug (CVE-2020-14511) in the framework web worker that can be activated just by sending a uniquely created HTTP demand, in the long run permitting assailants to complete far off code execution without the requirement for any qualifications.
Claroty specialists likewise tried HMS Networks’ eCatcher, an exclusive VPN customer that interfaces with the organization’s eWon VPN gadget, and found that the item is helpless against a basic stack-based support flood (CVE-2020-14498) that can be misused to accomplish far off code execution.
An aggressor should simply fooling casualties into visiting a noxious site or opening a malevolent email containing an explicitly created HTML component that triggers the defect in eCatcher, inevitably permitting assailants to assume total responsibility for the focused on machine.
Every one of the three merchants were informed of the weaknesses and reacted rapidly to discharge security fixes that fix their items’ escape clauses.
Secomea clients are prescribed to refresh their items to the recently discharged GateManager renditions 9.2c/9.2i, Moxa clients need to refresh EDR-G902/3 to adaptation v5.5 by applying firmware refreshes accessible for the EDR-G902 arrangement and EDR-G903 arrangement, and HMS Networks clients are encouraged to refresh eCatcher to Version 6.5.5 or later.





![[HINDI] What is DoS attack and DDoS attack?](https://bittentechsolutions.in/wp-content/uploads/2020/04/ddos-218x150.jpg)
![[HINDI] What is juice jacking? Think twice before using public USB ports](https://bittentechsolutions.in/wp-content/uploads/2020/04/juice-jacking-risk-1200x675-1-218x150.jpg)